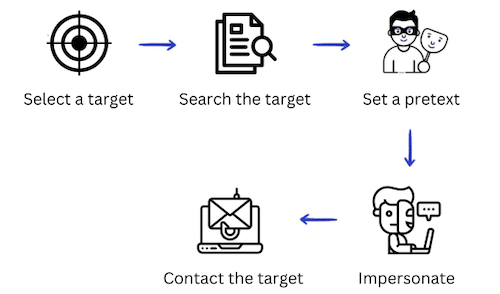
Email impersonation is often associated with malicious practices, such as Business Email Compromise (BEC), reputation damage, fake invoicing, and phishing schemes. The objective behind email impersonation is to defraud individuals or businesses of their money while staying anonymous through concealing the identity of the sender.
Within BEC attacks, scammers use impersonation to dupe employees into transferring money to a fake account, sharing financial information, login credentials, etc. Often they impersonate high-level executives within a company, such as the CEO or financial Director.
We also see victims being impersonated by someone with a more personal and malicious motive. Victims are framed, reputations damaged, and families destroyed.
This deceptive tactic finds common ground in spam and phishing attacks, where the overarching goal is to deceive recipients into believing that the message originates from a familiar or trustworthy source. Within these email spoofing incidents, the sender manipulates email headers, presenting a false sender address that is often accepted at face value by unsuspecting users. It’s only upon closer inspection of the email header that users may discover its fraudulent nature. The familiarity of a sender’s name can foster trust, increasing the likelihood of individuals clicking on malicious links, opening malware-laden attachments, divulging sensitive information, or falling victim to fraudulent invoices in BEC scams.
If you are reading this because you are looking for help with a Business Email Compromise, please consider engaging our BEC investigators.
How Does Email Impersonation Work
Email impersonation is different from hacking into an email account. Rather than compromising an existing account, email impersonation involves creating a disguise for an email, making it seem like it comes from a different sender.
The critical distinction lies in the fact that genuine email account hacking grants access to the owner’s contacts or enables the sending of spam emails, potentially damaging the email sender’s reputation. The success of email impersonation attacks hinges on the utilization of a Simple Mail Transfer Protocol (SMTP) server and an email platform like Outlook or Gmail. Perpetrators manipulate specific elements of the email header, including the FROM, REPLY-TO, and RETURN-PATH fields.
The most two common ways to impersonate someone through email are:
 Display Name Deception:
Display Name Deception:
Email impersonators often manipulate the display name to mimic someone familiar. Even if the email address seems legitimate, the display name may reveal inconsistencies.
For instance:
Real email address: name[at]rexxfield.com
Impersonated email address: name[at]rexfield.com
Look-alike Domains:
Attackers create domains that closely resemble legitimate ones, known as look-alike domains. For example, using “micros0ft.com” instead of “microsoft.com.” This technique aims to deceive recipients at first glance.
These impersonation scams are expected to only grow in numbers due to the rise of Deepfakes and AI technology. As technology advances, there’s a potential for email impersonation to involve AI-generated content or deepfake technologies. These could mimic the writing style and voice of individuals, making detection more challenging.
Tracing the Perpetrator Behind Email Impersonation
Tracing the individual behind email impersonation, requires a methodical approach and specialized tools. While challenging, our experienced cyber investigators combine a unique skill set and our own proprietary software to uncover the identity of the perpetrator.
Here’s a general guide on how to trace someone behind email impersonation:
Email Header Analysis:
Detailed Inspection: Examine the email header, focusing on information like “Received,” “From,” “Reply-To,” and “Return-Path.” These fields may contain clues about the origin of the email. Especially the IP address from which the email was sent is of interest. This information can help pinpoint the geographical location of the sender. In another article, we explained how to analyze email headers from Gmail, Outlook, and Yahoo.
Authentication Protocols:
DKIM (DomainKeys Identified Mail) and DMARC (Domain-based Message Authentication, Reporting, and Conformance): Check if the email adheres to these authentication protocols. Authentication results can offer insights into the legitimacy of the sender.
Digital Footprint Analysis:
Investigate the digital footprint left by the sender. This includes examining social media profiles, online forums, and any other publicly accessible information associated with the impersonated identity.
Email Service Provider Cooperation:
If the impersonation involves a major email service provider (ESP), reach out to their abuse or security team. They may assist in identifying the user associated with the email account. But we know from experience that most, if not all, email providers such as Gmail, and Yahoo, won’t disclose user information without a subpoena.
ISP (Internet Service Provider) Collaboration:
In cases where legal intervention is warranted, work with law enforcement or a lawyer to prepare subpoenas or court orders for ISP cooperation. This may reveal the identity of the person using a specific IP address.
We write subpoenas on almost a daily basis for clients and lawyers, and know exactly what to ask for. We can prepare a subpoena for a fraction of what you would pay a lawyer.
Legal Proceedings:
If the impersonation involves criminal activity, report the incident to law enforcement. They can conduct a formal investigation, issue warrants, and take legal action against the perpetrator.
Use the Expertise of Cybercrime Investigators
Rexxfield’s cybercrime investigators have expertise in email spoofing and impersonation cases and use advanced tools and techniques to trace the perpetrator. We also have access to proprietary databases, collaboration networks and deep dive intelligence. Relatively often, we can obtain data that even law enforcement can’t get.
Tracing someone behind email impersonation is a delicate process that often requires a combination of technical expertise, legal cooperation, and investigative skills. It’s crucial to follow legal procedures and work with professionals who understand the intricacies of cybercrime investigations.
Our cybercrime investigators can even bypass proxies and VPNs.
How to Recognize an Impersonated Email
Unsure if you are dealing with email impersonation? You can recognize an impersonated email by looking out for certain red flags:
- Name-Email Mismatch: Exercise caution if the displayed sender’s name doesn’t align with the email address.
- Signature Discrepancies: Scrutinize the email signature for inconsistencies compared to what you know about the sender. For instance, a claim of being in California paired with a Massachusetts area code in the provided phone number is a red flag.
- Inspect the Email Header: Take a closer look at the email’s header, specifically the “Received” line. It should align with the email address visible in the body of the email.
- Verify “Received-SPF”: Within the email header, check for a “Received-SPF” line. Ideally, it should indicate “Pass.” If it shows “Fail” or “Softfail,” there’s a heightened likelihood that the email is deceptive.
- Check DKIM and DMARC: In cases where the organization employs DKIM and DMARC, scrutinize the “AUTHENTICATION-RESULTS” in the email header. This section provides insights into whether the email adheres to the standards set by these protocols.
You can protect yourself from impersonation and hacking attacks through email security services like Mimecast.

 Display Name Deception:
Display Name Deception: