Investigating Email Spoofing
Email spoofing is a form of impersonation by email, often used for malicious harassment, Business Email Compromise, fake invoices, and other phishing and impersonation scams. The main purposes of email spoofing are impersonation to scam people or businesses out of money, or to stay anonymous by hiding an identity.
We help businesses who have lost hundreds of thousands of dollars to email spoofing and individuals who are harassed and defamed through anonymous emails.
Define Email Spoofing
Another reason people use a spoofed email address is to hide their identity to stay anonymous when harassing or threatening someone, or defaming someone to destroy their careers.
Email spoofing is possible due to the inherent design of email systems. Outgoing email servers typically rely on the client application to assign a sender address, making it challenging for these servers to distinguish between legitimate and spoofed addresses.
While recipient servers and anti-malware software can help identify and filter spoofed messages, not all email services have robust security measures in place. Therefore, users are advised to carefully examine the email header of each message to ascertain whether the sender’s address has been falsified.
How does email spoofing work?
Email spoofing is not the same as hacking into someone’s email account. It’s more like creating a disguise for an email, making it seem like it’s from a different sender.
For example:
Real: name [at] rexxfield.com
Spoofed email address: name [at] rexfield.com
The key difference is that when an email account is actually hacked, the hacker can access the owner’s contacts or use the account to send spammy emails, which can damage the email sender’s reputation. And this reputation is important because it affects whether your emails get delivered.
Email spoofing attacks are carried out using a combination of a Simple Mail Transfer Protocol (SMTP) server and an email platform like Outlook or Gmail. In these attacks, the person behind it messes with specific parts of the email header, like the FROM, REPLY-TO, and RETURN-PATH fields.
The reason this spoofing is possible goes back to the early days of email. Email systems separate the message headers (which include stuff like TO, FROM, and BCC) from the actual email content. Unfortunately, when the SMTP protocol was created, it didn’t include strong security measures, so it can’t really verify the authenticity of email addresses.
How to Recognize a Spoofed Email
Here are some clues that might suggest an email is not what it seems:
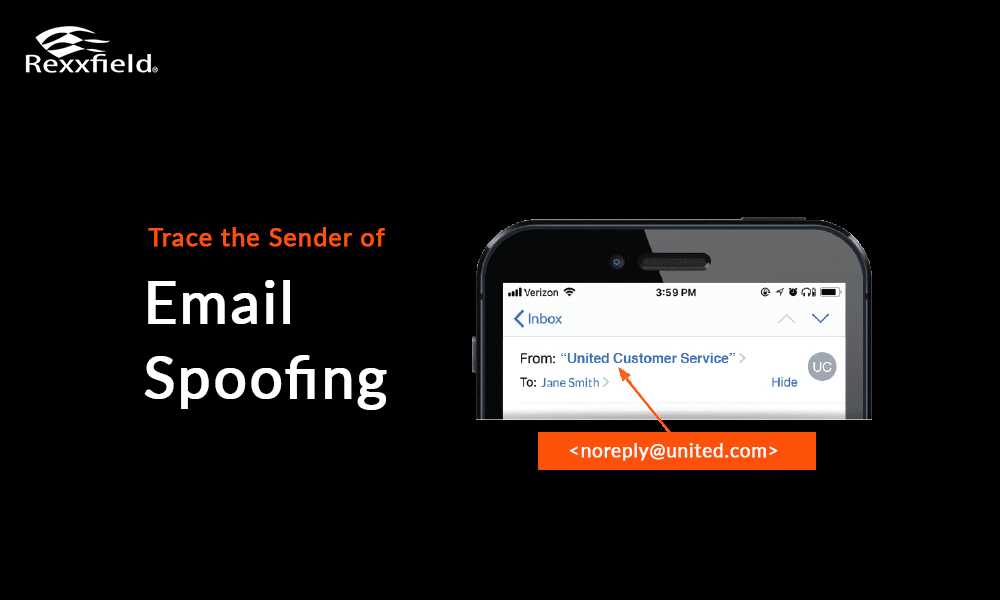
Name Doesn’t Match Email: If the name shown as the sender doesn’t match the email address, be cautious.
Signature Doesn’t Add Up: Check for any differences between the info in the email signature and what you know about the sender. For example, if they say they’re in California but provide a phone number with a Massachusetts area code, it’s a warning sign.
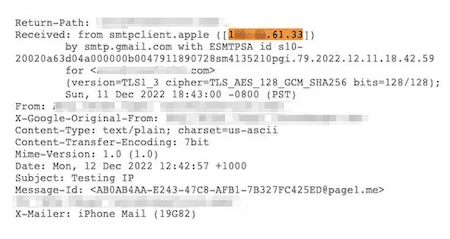
Check the Email Header: Take a peek at the email’s header and check the “Received” line. It should match the email address you see in the email.
Check “Received-SPF”: In the email header, see if there’s a “Received-SPF” line. It should ideally say “Pass.” If it says “Fail” or “Softfail,” there’s a higher chance the email isn’t what it claims to be.
Check DKIM and DMARC: If the organization uses DKIM and DMARC, look at the “AUTHENTICATION-RESULTS” in the email header. It’ll tell you if the email meets the standards set by these protocols.
How to Trace the Email Spoofing Sender
Tracing email spoofing and pinpointing the person behind it is no walk in the park, but our cyber crime investigators have proprietary advanced tools that often do the trick. These techniques for identifying email spoofing culprits are much like the ones we’ve fine-tuned to uncover anonymous Twitter users and spoofed text messages in various internet crime cases.
When the spoofed email address is still active and can receive messages, our investigators can follow the trail and identify the individual responsible for the email spoofing, often without needing to go through the hassle of subpoenas. Even if the email address is no longer active or abandoned, don’t lose hope. We can assist your legal team through the legal discovery process. Even better, if there’s a criminal angle to these messages, we can help you to get law enforcement to join the effort. With the police on the case, you won’t have to pay fees for private lawyers, and you can get answers much faster.
Trace the IP address from a Spoofed Email Address
There are several ways to trace an IP address from a spoof email address. One you can do yourself: analyse the email header and its metadata to find an IP address.
Gmail spoofing
Gmail often doesn’t disclose the IP address of users, but to be sure, follow these steps to find out if the email header reveals the IP address of the sender.
- Click the three dots at the right corner of the email
- Click on “show original”
- Click on “copy to clipboard” and paste it into an email to send to you.
- OR select all the code, right-click copy, and paste it into an email.
If you have found an IP address from the Gmail spoof email address, go to Infosniper.net, enter the IP address, and that will give you a location, such as the city the sender is in. It’s important to understand that an IP address can only give you a rough idea of where the sender might be at a given time. When you trace an IP address, you can obtain basic details like the Internet Service Provider (ISP), the state, and the city.
However, there’s a significant twist to this. If the user is employing a VPN, proxy, or the Tor Network, it becomes quite challenging to pinpoint the owner of an email address. Not even Google or Protonmail can provide the real IP address in such situations. But here’s where we come in: our investigators often have the means to bypass proxies and VPNs.
Rexxfield has developed its own unique tool for combating cybercrime, enabling us to identify anonymous internet users. In cases like these, we can assist you in uncovering the IP address from an email address. Rest assured, all our methods are not just legal but also persuasive and admissible in court.