A little known scam type has become the most lucrative type there is. Are you at risk? Is your business at risk? It’s called Business Email Compromise or BECs for short, and in 2022 on average each victim lost USD$125,000. If you own a business or are a business executive or general manager with authority to move money around, then you are at risk unless you are following at least these six safeguards.
Business Email Compromise
Not long ago, Rexxfield’s senior private investigator, Anna Brown dug deep into business email compromise. I’m not going to repeat her deep-dive here, but rather I’ll reinforce from the latest statistics how important it is for you to be alert, and what you can do to stay safe. Then lastly, what to do if you suspect you are a victim.
Recap: What is Business Email Compromise (BEC)
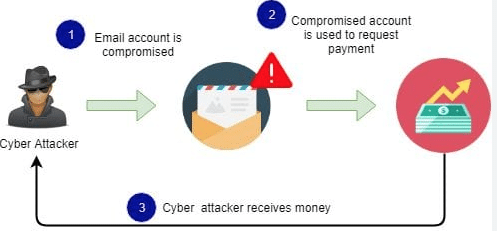
Business Email Compromise is the term given to techniques that fraudulently use email to scam unsuspecting people into making money or payment transfers that result in funds being stolen.
Anna went into some of the many ways that can happen, which you can recap in her deep dive.
But in all honestly, the variations are growing all the time as a cat and mouse game continues between the perpetrators and those of us who combat it. These are most of the common types of business email compromise:
- Malware
- Spearphishing emails, and
- Website impersonations.
Malware
Malware involves getting malicious code onto your computer or network, spying on confidential information, capturing keystrokes, gaining access to emails, invoices, passwords and other sensitive data which can be used to deceive or even control the user’s account.
For example, malware could be used to gain access to the email account of a General Manager. When that GM is distracted or away, the intruder could send emails to others in the organisation or to customers or to vendors. They appear legitimate, as they are from the GM’s real email account. The fraudster may ask for a bank account change for payments or other believable messages, and by the time anyone has picked up on the change, thousands of dollars may have been diverted to a fraudster’s bank account.
Spearphishing
Spearphishing can work in a similar way, but instead of the emails coming from the legitimate account, they are an imitation that at first glance, look legitimate. They take you step by step down a path that eventually leads to compromised security and data loss.
Kaspersky security says this about spearphishing:
An email arrives, apparently from a trustworthy source, but instead it leads the unknowing recipient to a bogus website full of malware. These emails often use clever tactics to get victims’ attention.
Email Impersonation
Email impersonation doesn’t come from a legitimate account, but it looks like it does. Subtle differences in the email address can be overlooked at first glance, and can be used to convince the receiver to reveal confidential data. They can also take the receiver to imitation websites or install malware. These imitations are getting harder to spot. You need to be ever vigilant to make sure the email sender is who you think they are.
For example, can you spot the difference?
[email protected] vs roger.daví[email protected]
FBI IC3 2022
BEC value lost:
2020: $1,866,642,107
2021: $2,395,953,296
2022: $2,742,354,049
Value lost has increased by 50% in just 2 years!
Sadly, when it comes to BEC, crime pays.
Unfortunately, Business Email Compromise is high reward from a relatively low risk.
Don’t be a Victim of Business Email Compromise
So in the short term, Business Email Compromise can not be stopped. It therefore comes down to how well you protect yourself so that you do not become a victim.
What can you do to protect yourself?
Your business should start with having strong multi-stage protections against the movements of large sums of money. This is inconvenient, due to all the extra administration and controls, but the consequences are just too high if you do not take business email compromise seriously.
These are some things you can do, and you should probably do more than just one or two:
- Get knowledgeable and push for others in your business to do likewise, instigating a policy of regular training for people who have authority over payments
- Multi-people authorisation of transactions. For example, transactions over a certain size require more than one person to authorise payments or changes.
- 2FA. Use a multi-factor authorisation process, and probably something more secure than Google.
- Remind your customers and vendors to be suspicious. There is a reason you get those ‘beware of scams’ messages from your bank. Be alert and help others to be alert too.
- Have a good password policy and enforce it. As a minimum, force the changing of passwords regularly, don’t allow reusing of passwords, make sure they are not the name of your first dog. ‘Rover1’ is not a good password!
- Review your banking authorisations and limits to limit banking operations to minimise the damage if a compromise does happen.
In a nutshell, it boils down to your policy and your business compliance to that policy.
“Policy sets out the rules, but a lack of compliance to policy leads to complacency and complacency leads to risk. Risk unaddressed leads to loss.” – Guy Snow.
Lastly, don’t fall into the “It’s not my job” crowd.
If you don’t act, it could be “your job” and the jobs of many others.
Business Email Compromise scammers are hunting for victims. Don’t be one.
What to do if you suspect that you are a Victim
If you suspect you are a victim of business email compromise, you need to act VERY fast. Statistics show that if you haven’t acted decisively within 72 hours, the money will be nearly impossible to recover (depending on how and where).
First, contact your financial institution and tell them what’s happened. Find out if the transactions can be reversed.
Next put a block on any new transactions, that may come through any of the compromised systems or people.
Stop the bleeding before you try and figure out how it happened and how to fix it.
Once you’ve done what you can there, it’s time to contact Rexxfield.
Our team will get straight to work investigating what happened, investigating suspects (if you have any) and piecing together a picture of what transpired.
You should also contact law enforcement, but contact us first because we can advise you how to approach law enforcement and what to do should you hit a brick wall.
Please go and complete a Crime Report, and we will be in touch within 24 hours.


