This Intelx.io case study contains the results of Filip Flint’s (OSINT investigator at Rexxfield) investigation and the resulting compilation of the digital forensics available through open source clear and dark web media. His investigation is geared toward unraveling bad actors’ networks, patterns in criminal activity and the unmasking of the perpetrators.
In this case study, the statements are derived from his experience and the information shared by the victims involved in the case. It’s important to note that he does not assume responsibility for any inaccuracies, alterations, or omissions in the provided information, whether intentional or accidental.
Our client fell victim to an elaborate online scam, resulting in a substantial financial loss exceeding $1 million. Given key information provided by the client, including details about the scam domain and the scammer’s email, our cybersecurity investigation aimed to identify and apprehend the perpetrators responsible for this fraudulent activity.
Challenges
- Limited Initial Information:
The investigation commenced with minimal details, posing a significant challenge in tracing the perpetrators. The only leads available were the domain and email associated with the scam.
- Sophisticated Scam Operation:
The scam exhibited a high level of sophistication, indicating that the perpetrators were well-versed in cybersecurity evasion techniques. This complexity made it difficult to trace the individuals behind the scam.
The email was freshly made just for the scam, and no additional leads were found from it. It was a dead end.
Role of Intelx.io in the Investigation
- Initial Search on Intelx.io:
Our first step involved leveraging Intelx.io to search for information related to the scam domain.
- Discovery of “Stealer Log”:
Through Intelx.io, we found a “stealer log” associated with the scam domain. This log proved to be a critical breakthrough, revealing that the scammer’s PC was infected with malware.
Key Information Extraction
The infected PC provided a wealth of crucial information for the case, including the suspect’s name, details of other criminal operations they were involved in, as well as insights into their location and money laundering techniques. This newfound information significantly advanced the investigation.
The malware captures all the browser information, like browsing history, cookies, passwords, and autofill details.
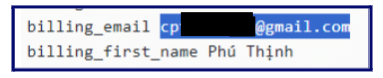
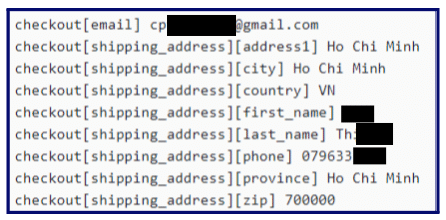
- The stealer log revealed an extensive network of email addresses used by the suspect.
Beyond the initially provided email, we identified additional email accounts associated with the scam domain.
- Multiple emails share the same password, and they were all logged on the same machine, which indicates that the same user is behind these emails.
One of the emails had admin access to the scam domain.
- Suspect:
A name was found connected to some of the email addresses:
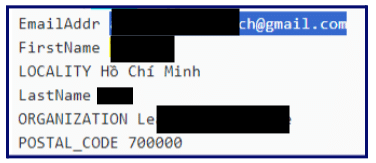
This is the (autofill cookies) information that the browser (Chrome) stored on the infected computer.
The above image shows that the same name was found to be connected to the email address used for scams.
Google Docs
In the leak of the suspect’s Chrome search history, Google Docs were found. One of the documents appeared to be an accounting document.
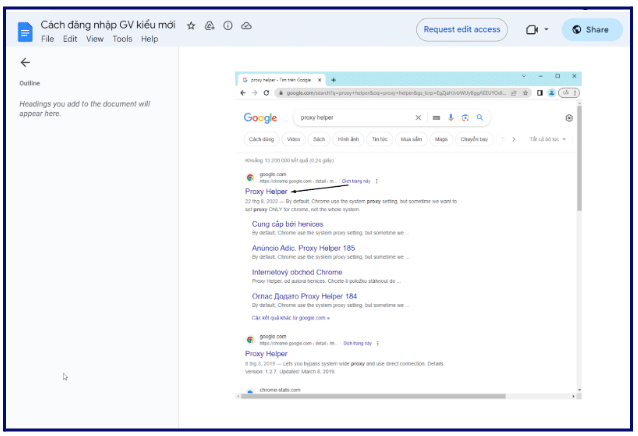
Another document found teaches how to set a proxy and hide your IP, as well as how to set a VOIP number:
Here we can see that they are using the username that represents the scam, which implies that they are using this guide to train people to obfuscate their identity, possibly for scamming.
The owner’s name of the documents is the same name connected to the email addresses. This owner has a profile photo, but it should not be discounted that the individual is using a fake profile picture.
He is editing the documents, which suggests some level of authority, ownership, or manager or control in the scam syndicate.
Uncovering the Criminal Network with Intelx.io
Intelx.io played a pivotal role in unraveling a broader criminal network connected to the scammer. The platform allowed us to identify additional criminal operations, providing a comprehensive understanding of the group’s activities. These operations include fake betting websites, fake escort services and more scam domains.
Location and Money Laundering Techniques
By analyzing the data obtained through Intelx.io, we were able to pinpoint the location of the suspects and gain insights into their sophisticated money laundering techniques, contributing to the overall intelligence gathered for the case.
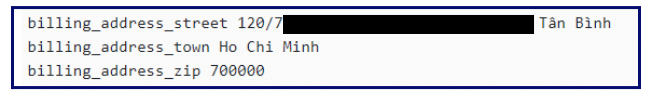
- An address was found in the breach:
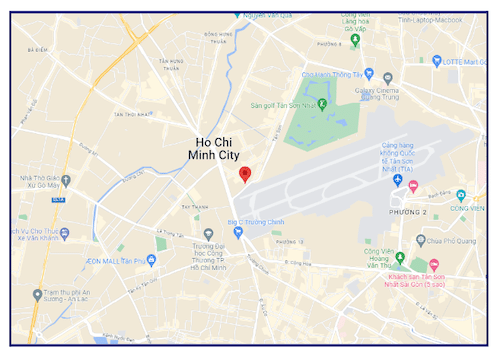
(Google Maps screenshot of the location)
Further search for the address led to a helmet manufacturing company in Vietnam (company name not disclosed in this case study).
On the same PC, the perpetrator was logged in on an email connected to the scam domain, as well as the email connected to this helmet manufacturing company, and they all shared the same password. The name of the company matches two emails found in the breach. Note that these emails were logged on the same computer as the email addresses used for scams.
Through Intelx.io, we found that both email addresses share the same password. This indicates that our suspect has connections with both the helmet manufacturing cover operation and the scam operation.
How Intelx.io Improves Our Crypto Investigations
Intelx.io has become a crucial tool in our crypto investigations, enabling us to bridge the information gap, uncover hidden details, and dismantle sophisticated scam operations.
The intelligence obtained through Intelx.io played a pivotal role in identifying the culprits, and their criminal network, and advancing the case towards a successful resolution.
This case underscores the significance of threat intelligence tools like Intelx.io in combating cybercrime and safeguarding individuals and organizations from online scams.
In our online investigation, we found a suspect by checking breached and leaked files. We also found a name, DOB, director ID and potential business address for the office holder for the fraudulent companies. These are strong leads, and there is considerably more data that can be uncovered, for a criminal or civil investigation, best obtained under law enforcement or court authority.