Pig Butchering Scams: Combining Romance and Crypto Deception
In recent times, the realms of online dating and cryptocurrency have become breeding grounds for deceitful activities. As the popularity of online dating continues to rise, fraudsters have seized the opportunity to exploit vulnerable individuals seeking companionship. Similarly, the allure of cryptocurrency gains has given rise to a surge in crypto scams. Amid this evolving landscape, a particularly concerning scam has come to light, blending the emotional manipulation of romance scams with the cunning tactics of crypto cons—a scheme aptly referred to as “Pig Butchering Scams.”
This multifaceted scam has its origins in China and specifically targets individuals across the globe via dating platforms. Victims of the Pig Butchering scams are enticed with promises of affection and substantial crypto earnings, only to find themselves trapped in a web of financial devastation and emotional turmoil. The fraudsters behind this elaborate con invest months in cultivating trust with their targets, using a combination of romantic overtures and tantalizing crypto prospects to strip victims of their savings, leaving them grappling with lasting psychological and financial scars.
How Pig Butchering Scams work
Operating as part of a crypto scam syndicate, the Pig Butchering fraud ring scours dating apps for potential victims. This deceitful scheme capitalizes on victims’ emotions through excessive displays of affection—often referred to as “love bombing”—and the tantalizing promise of crypto riches.
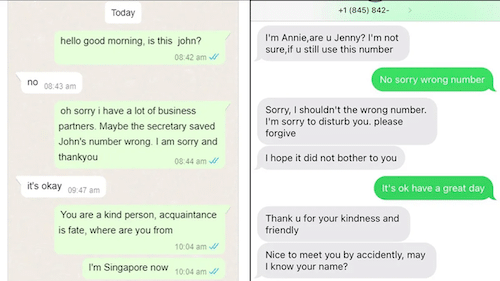
Transitioning to Offline Platforms: Once initial conversations foster trust, scammers attempt to move the dialogue to encrypted messaging apps like WhatsApp to maintain anonymity and evade detection.
Grooming the Victim: The targeted individuals are initially showered with affection, romantic messages, and promises of luxurious international trips and extravagant gifts. This approach builds credibility, setting the stage for manipulation.
Manipulation and Financial Pressure: After building a connection, fraudsters employ psychological tactics to make victims feel insignificant, compelling them to take actions to regain self-worth. As discussions turn to in-person meetings, the scammers invent excuses to maintain a virtual relationship.
Introducing Crypto Investment: Conversations inevitably shift to cryptocurrency investments, with scammers touting their own impressive gains and offering to mentor victims for additional earnings. This strategy capitalizes on the growing interest in crypto but limited knowledge among newcomers.
Catfishing for Crypto Gains: Victims are instructed to create accounts on legitimate crypto platforms before being directed to a fraudulent crypto trading exchange controlled by the scammer. The exchange, mimicking real platforms, only accepts Tether (USDT) and displays manipulated returns to instill confidence.
Deception and Disappearance: After siphoning funds from victims or when victims realize they can’t withdraw funds, scammers vanish. Victims are left financially drained, and the scammer disappears from the dating app.
Help for Victims of Crypto Scams
If you have a budget to seek professional assistance, please provide the specifics of your scam through our contact form. We will investigate to let you know if a recovery is feasible.
CAUTION: The sole viable avenue to potentially retrieve your crypto assets is by involving law enforcement, obtaining subpoenas, and pursuing legal action.
It is essential that any credible recovery strategy incorporates law enforcement. Rexxfield follows this proven approach for success:
Crypto Tracking + Open-Source Intelligence (OSINT) + Social Engineering + Subpoena
Should a recovery service present an alternative narrative, exercise caution and consider it a RED FLAG. Refrain from investing your time or resources with such entities.
Before you decide to have Rexxfield or some other firm investigate pig butchering scams, take a few minutes to read this article about how recovery does NOT happen, and how it could happen. Remember: recoveries are rare, don’t buy into guaranteed recoveries and big promises.
Our Approach to Investigating Pig Butchering Scams
Compiling Evidence to Establish Proof
At Rexxfield, we hold licenses and certifications for premier blockchain tracing tools, akin to those employed by the FBI and Secret Service. Utilizing these tools, we conduct a meticulous forensic examination of the blockchain to trace the movement of funds from your wallet to the scammer’s wallet and across the network. In parallel, we engage in Open Source Intelligence (OSINT) to uncover digital traces on both the visible internet and the Dark Web. By amalgamating these findings, we construct an evidence dossier that is tailored for law enforcement purposes.
Transferring the Evidence to Law Enforcement
Our evidence package includes a report meticulously designed for law enforcement consumption. This report, a collaborative effort between our adept team and our ex-FBI liaison officer, is consistently refined based on real-time feedback from law enforcement. We ensure that your case finds a suitable home within law enforcement agencies. This package, containing our findings and evidence, serves as a solid foundation for their subsequent investigation, saving them substantial time in fulfilling the proof requirement.
Police Investigation
Upon commencement of an inquiry, a law enforcement agent establishes direct contact with the victim. Over time, a decision may be reached to procure a warrant affidavit for identifying the scammer’s identity from a cryptocurrency exchange, which is subject to KYC, CTF, and AML regulations, through which the stolen cryptocurrency has transited.
Prosecution and Seizure Implementation
Should the law enforcement process be robust, a prosecutor might opt to take on the case. If all goes well and the cryptocurrency remains partially or entirely within the exchange, the prosecutor seeks a court-issued warrant for freezing and seizing the stolen assets.
Anticipating Recovery Time
However, it’s important to note that swift recovery is not guaranteed. In some instances, a court-ordered freeze can last for over a year without funds being returned to the victim. This delay arises because the proceeds of crime can be held as evidence. Additionally, cases involving multiple victims claiming the same assets can lead to a complex disbursement process, which demands time to resolve.
Regrettably, this legal route is gradual, and victims must be prepared for an extended timeline if they’ve lost cryptocurrency to a scam.
Can We Recover Your Stolen Funds?

We are acutely aware of the emotional toll on victims who approach us with hopes of recovery, only to find out later that we are unable to proceed with their case. Our commitment is to mitigate disappointment and avoid adding further distress to those who have already suffered substantial losses.
Challenge: Overseas Police Corruption
Numerous challenges arise, particularly when dealing with instances of police corruption in Southeast Asia. In certain situations, corrupt law enforcement officials may provide scam managers with a window of two or three days to relocate (once their location has been identified) in exchange for substantial bribes. To counter such issues, we exercise extreme caution by implementing robust, independent oversight and scrutiny mechanisms prior to involving local authorities.
Rexxfield’s investigative efforts uncover the IP addresses of foreign scammers, commencing from the initial boiler-room setups and progressing to higher echelons of management in locations like Hong Kong, mainland China, and beyond. Subsequently, we refer the case to Western federal law enforcement agencies for cross-border stings, with the intention of introducing heightened scrutiny that could curtail corruption in the developing nations.
Challenge: Law Enforcement accepting your case for an investigation
The challenge is that the total losses, while considerable to you or I, are unfortunately too low for the FBI, or another federal agency, to commit any resources to an investigation without an overwhelming amount of evidence or a positive identification and location of the scammers.
We’ve been advised that if a case has a loss under $500K the DOJ agencies we refer cases to are unwilling or unable to assign the case to a field office.
This case loss threshold is somewhat of a moving target, last year it started at $150K, by the summer the threshold moved up to $250K, and by the end of the year it was $300K.
It is simply a factor of the sheer number of cases being submitted to them at the moment. In 2022, more than 800,000 BEC and crypto scam reports were submitted to the IC3. And this number increases every year.
As you can imagine, that’s an impossible number, especially when you factor in there are a little over one thousand cyber-trained FBI agents.
However, all is not lost and you can still pursue an initial crime report with a State, County or Metro level law enforcement agency.
These different police authorities have the same subpoena power federal agents have, and that’s all that’s required to kick start an investigation.


